



Swipe
The KeyWatcher and KeyBank can work as single cabinet systems or designed with scalability in mind, each system can consist of multiple add-on cabinets securing thousands of key sets all controlled by a single console. It’s easy to expand as your needs grow.
The new large 7″ touch screen key register systems give you a common smart device interface. But that’s not all that’s new. Software database changes and transaction collection updated in real-time! If your company has multiple KeyWatchers, with users that need access to one or more KeyWatchers, there’s now a global user database allowing you to simply select which KeyWatcher(s) each user can have access to. Global Profiles determines a user’s access. There’s an on-screen scrollable list of key sets and groups the user has access to creating an intuitive user experience. We just keep making key management better.
Of course, you still get our fully scalable modular design. The latest KeyWatcher Key Management System offers you a new touch screen for easy user navigation. Its illuminated key storage system makes finding keys a cinch, while using minimal wall space. The random key return comes standard to allow you to return any key set to any slot, eliminating the confusion and worry of misplaced key sets. feature allows you to return any key set to any slot, eliminating the confusion and worry of misplaced key sets. That’s Morse Watchman’s’ outside the box thinking – right inside the box.
The Morse access control and audit tracking key management systems offers tight security and eliminates manual log errors with an indisputable audit trail. Reduces the number of times you might need to re-key from people unintentionally take-home keys and frees up manpower for other important duties!
Removing key sets from the KeyWatcher is as simple as a user entering their User ID and PIN, or as sophisticated as requiring 1 to 3 users to login in using an access card or fingerprint reader. You have peace of mind in knowing that the door does NOT open until an authorized user(s) login in and the user(s) has access to the pre-selected key set(s). Multiple Sets only require a single login for each authorized user. The KeyWatcher automatically records this information in a database to provide you with a complete and indisputable audit key report trail. Unauthorized access can trigger alarms locally and centrally. You can also locate which KeyWatcher Touch a specific key is in, or determine who has it out, with the new KeyFind feature.
- Large 7″ full color, touch screen
- Common database for all KeyWatcher systems
- Real-time syncing of database changes
- Real-time transaction collection
- Easier key removal – user select from a list of keys that a user has access to
- Status bar guides users on what to do, and shows what is happening
- “Find Key” determine if a key is out and with who or In and where
- “My Keys Out” allows users to see which keys they have out, if any of their keys are overdue, and when their keys will become overdue
- UserID can be the EmployeeID number
- Profiles provide an easy way to assign key and group permissions, access level, and much more to users
- A client / server based, Enterprise Solution, SQL system and service
- Enter custom notes and information via on-screen QWERTY keyboard
- Reports utilize color and include more information including portrait and landscape modes
- Scheduled Reports feature lets users create reports, save criteria and schedule each report to be run automatically and emailed, saved or printed
- Text/email notifications enable users to create alerts for specific users, keys or events and select who will be alerted
- Improved integration interface for 3rd party software
- Optional “KeyAnywhere” allows keys to be returned to any KeyWatcher Touch system.
- Locking locations for increase security
- Random key return allows key sets to be returned to any location (non-random key return is optional)
- Easy to locate any key set with the illuminated key slots
- Accountability by time, date, and user codes
- Time zones can be assigned to each individual key and different for each user
Built into a rugged steel cabinet with highly illuminated key slots, the improved design makes it easier to locate keys and maximize wall space. The exterior design of the cabinet has been enhanced to blend in with today’s office environments, while the key management system seamlessly controls and monitors keys.
Built using stainless steel, the cabinet is designed to resist abuse and is wired to alarm against tampering. Yet, the system has limitless configurations – allowing the ability to scale the key management system as needs expand.
Morse Watchmans makes it simple for you, as the KeyWatcher and KeyBank can hold keys of almost any size, including Folger Adams keys. Plus, the systems are capable of incorporating additional lockers for valuable items.
Each key storage system is powered by AC electricity and is supported by a 24-hour battery backup power supply.
- Each key is individually locked in place.
- Card access and biometric reader compatible
- Random key return eliminates pattern checking (non-Random return is optional)
- Require a “Reason Why” note to be given before removing and/or returning specified key sets, including an optional requirement for a comment
- “Instant Key Release” for users that have access to one key set or group. (Upon login the system knows if the user has the key set or not. If they don’t it opens the door and gives it to them. If they already have it, the door opens to return it.)
- Require up to 3 user logins’s each from a different department
- Medco lock with tamper-proof plate
- See-through doors (optional)
- Tampering with the KeyWatcher or Smartkeys triggers an alarm
- Overdue key alarms configured by time period or duration
- Numerous alarms types
- 24-hour battery backup
- Six Alarm relay contacts for remote notifications
- Door does NOT open until system determines user(s) authorization to requested key set(s)
Call and ask our knowledgeable sales staff about these high security and automation features
- Instant Key Release
- Groups Release
- Dual/Triple User Access
- Departmental Access requirement
- Secure Key Return
- Reason Why for key removal and/or return

The KeyWatcher and KeyBank systems are identical with exception to one feature. The KeyWatcher has locking locations. The KeyBank has non-locking locations, and therefore is less secure and available for a substantial lessor price. With the KeyWatcher, when the door is open, only the key set(s) that were requested and determined authorized can be removed. All other sets are locked in place. With the KeyBank system none of the key sets are locked in place. Therefore, even users that are not supposed to have access to a key set can still remove it. However, a record of authorized and unauthorized key set removals will be created.
A variety of access control devices to interface with
Like a door to a building or room, the KeyWatcher stands by waiting for a valid signal from your preferred method of access validation. The KeyWatcher comes with a standard touch screen. Users enter a 4-6 digit UserID and a 4-digit PIN. There are also other available access methods as detailed below.

The initial standby Start screen mode.
4-6 Digit UserID + 4-Digit PIN Combination Login
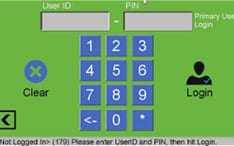
From this screen a user can either enter a 4-6 digit UserID and a 4-digit PIN or use one of the other two optional methods below. Note that you can also optionally disable UserID login when Fingerprint or card readers have been implemented.
Fingerprint (most common method)

An image of the fingerprint is NOT stored. Instead the unique reference points of a fingerprint called minutiae points or PK’s. These are bifurcations (splits), end of ridges, etc. Using algorithms, a mathematical score is created from these PK’s for referencing against future biometric comparisons. The information from a stored template CANNOT be recreated to duplicate the user’s fingerprint. The stored template is proprietary to a MorphoTrak system and CANNOT be used for any other function such as background checks, law enforcement, or civil identity systems.
Card Reader Login Option

Your choice of magnetic card strike or proximity RFID card readers and be integrated to eliminate entry of UserID. The system can be configured to optionally require a PIN number with the card read.
Card Reader Relay Input Option
This feature allows the KWTouch login to be locked at all times, unless the relay input has been triggered by a valid reply from your access control system.
How it works:
The KWTouch has an input connection on the optional Card Reader/Relay board. This normally open input is monitored by the board. When there is a momentary closure between the RLY and GND connections, the system will unlock the touch screen and allow login input.
Login Input methods allowed after unlocking:
- Fingerprint scan
- Secondary card reader directly interfaced with the KeyWatcher
- Single card reader: The weigand wiring can be split to connect to your access control system and directly to the KWTouch. The 1st card swipe would unlock the KWTouch and allow for a 2nd swipe on the same card and reader to login to the KWTouch for key access.
Once the user logs out, the system is automatically relocked.
Note: Once the relay input is activated, the system will be unlocked waiting for a login for 10 seconds. If no activity is detected, then the system will relock waiting for the relay input.
Example of Use:
- If the KeyWatcher is in an active area or has public access where the system could be subject to tampering.
- A card reader connected to an access control system would be placed next to the KWTouch.
- The access control system would need to verify the card swipe, then make a momentary closure across our relay input contacts. This would activate our system.

1 Module Touch Screen Key Cabinet System
- Single module system accepts all standard KeyWatcher modules.
- 6, 8 & 16 location SmartKey modules, Card/Credit Card module, Single and Dual Locker modules.
- Compact key organizer cabinet system fits almost anywhere.
- Comes standard with the bottom mounted control box, but can be used with a remotely mounted keypad and display box.

2 Module Touch Screen Key Cabinet System
- Two module system accepts all standard KeyWatcher modules.
- 6, 8 & 16 location SmartKey modules, Card/Credit Card module, Single and Dual Locker modules.
- Compact key organizer cabinet system fits almost anywhere.
- Comes standard with the bottom mounted control box, but can be used with a remotely mounted keypad and display box.

3 Module Touch Screen Key Cabinet System
- Three module system accepts all standard KeyWatcher modules.
- System contains up to 48 SmartKey locations per key organizer cabinet, and supports additional cabinets.
- 6, 8 & 16 location SmartKey modules, Card/Credit Card module, Single and Dual Locker modules.
- Expandable – if future growth demands the need for more keys, modules or add-on cabinets can be added to increase the capacity of the system.
- Comes standard with the bottom mounted control box, but can be used with a remotely mounted keypad and display box.

6 Module Touch Screen Key Cabinet System
- System contains up to 96 SmartKey locations per cabinet, and supports additional cabinets.
- Six module security key cabinet system accepts all standard KeyWatcher modules.
- 6, 8 & 16 location SmartKey modules, Card/Credit Card module, Single and Dual Locker modules.
- Expandable – if future growth demands the need for more keys, modules or add-on cabinets can be added to increase the capacity of the system.
Modular, Scalable Design Lets You Customize Your KeyWatcher System

The KeyWatcher system is easily expandable. A system of any size can easily be configured by adding pre-built modules, so you can economically build your own system to suit your individual needs. Each module can hold 6, 8 or 16 key set locations; or a module can consist of locker or credit card holders. Manage as few as six key sets or take control over hundreds or even thousands.
From a single key management system to multiple key control cabinets holding hundreds of keys, it’s easy to expand KeyWatcher as your needs grow. Each additional unit can be controlled by a single console and monitored by the advanced KeyPro software.
The KeyWatcher key box cabinet can hold keys of almost any size, including Folger Adam keys. Plus, the systems are capable of incorporating additional lockers for valuable items. Available modules include 16-key, 8-key, 6-key, card, and a variety of locker sizes. These key modules can be customized in a wide range of cabinet sizes.
Key Set and Card Modules

6 Key Set Module
Great to Folder Adam Keys or Key Caddies

8 Key Set Module

16 Key Set Location Module
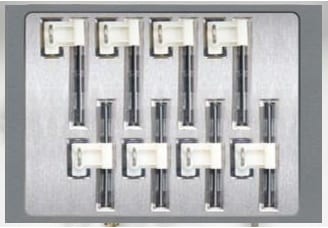
Credit/Access Card Module
Thin slots are ideal for credit card, gas & access cards
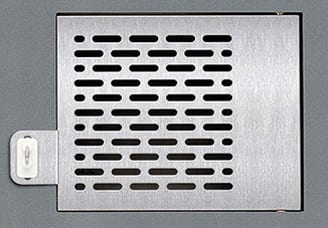
Single Locker Module

Dual Locker Module
Spacious lockers hold large items such as prescriptions, small firearms, cell phones, etc
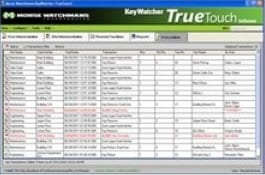
TrueTouch Client PC Software
KeyWatcher TrueTouch key inventory software comprises the KeyWatcher TrueTouch client interface and the KeyWatcher Server for enhanced administration and control of the KeyWatcher Touch system.
Key Inventory Software Features:
- Client Server Enterprise solution using a dedicated application server and SQL DB.
- Server performs all synchronizations of DB changes and transactions
- Auto-sync for automatic updates of KeyWatcher systems as changes are made.
- Auto collection of transactions as they occur
- Profiles to quickly assign users key and group permissions, access level, and many other settings to Users
- Text/email notifications enable users to create alerts for specific users, keys or events and select who will be alerted
- New, easier to read reports utilize color and include more information including portrait and landscape modes
- Reports feature lets users create and save reports with custom criteria for easy future access
- Reports can be scheduled to be automatically emailed
- All reports can be saved in PDF and CSV file formats
KeyWatcher TrueTouch client interface is designed to run all programming, remote functions and reports for many KeyWatcher Touch locations. Add users from a global list and all specific settings (added or modified) will be automatically synchronized across the system. Share Fingerprints or Card Access across multiple KeyWatchers with a single enrollment. Profiles make quick work assigning KeyWatcher access for improved user control. Administrative access levels are designed to allow reports only or alarms only in addition to the five system administration levels.
Generate TrueTouch reports in landscape or portrait format with color interspaced lines for easy reading. Reports can be scheduled to automatically email, print or save.
The KeyWatcher TrueTouch Server is designed for installation on a dedicated computer and can be connected to a KeyWatcher via a network connection. The server is the main interface for the client software and performs all synchronizations of transactions as well as maintaining the SQL database. Both access control systems and customized client control software interface with the server application.
It’s all done with the express intent of addressing your specific security needs with the most cost-effective, end-to-end solutions.
The new "Home KeyWatcher" configuration options! Have it your way!
This unique unparalleled configuration provides flexibility in where your key sets can be returned.
- Random: Return key to any KeyWatcher and any slot on the same site. Otherwise known as "KeyAnywhere".
- By KWTouch: Return to specific cabinet, but any slot within a specific KeyWatcher system
- By KWTouch and Box: Return to specific slot and cabinet within a specific KeyWatcher system
- By KWTouch, Box and Slot: Return to specific a KeyWatcher, cabinet and slot
If the need arises, there's unique configuration called "KeyAnywhere" that allows a key set to be returned to AnyWhere in ANY KeyWatcher, and easily locate which KeyWatcher it's in.
Remote Touch Screen


This is an example of the optional Remote Display for use in an industry such as casino's were the KeyWatcher cabinet would be mounted just outside the cage securing sensitive key sets, and the remote display on the inside. Or in a correctional facility the cabinet would be inside the control room and the remote outside it. This configuration is beneficial when there are key sets that require more then one user login before they are released.
Multi User Key Removal & Returns
Key Removals: The ability to control how many total logins will be required for a user to remove the key. Changing this will default the number of logins required for returning the key to the same setting. The number of logins required for returning the key can be independently changed, however. This feature is useful in cases where two people are required to be present during the key removal.Key Returns: The ability to control the total number of logins that will be required for a user to return a key. The number of logins required will be initially set by the number of logins required for removal. However, it can be changed to another setting if desired. This feature is useful in cases where three people are required to be present during the key removal.

