Smart Lockers




Swipe
SmartKey electronic locker systems are the solution for securing, controlling and tracking larger objects. Now access to laptop computers, cash trays and more can be managed as efficiently as keys. Items can be returned to any security locker system for convenience.
Set up SmartKey Locker systems as a personal metal locker storage space for one or multiple users. Like all Morse Watchmans solutions, they are customizable and scalable.
SmartKey metal security locker cabinets are engineered for complete interactivity with your other business systems. By opening our protocols to a wide range of integration partners, Morse Watchmans makes it possible for you to implement connectivity across systems on any level you choose. For example, by integrating your SmartKey Locker system with your access control system, your access control system will know which users are in the facility and which are not. A user who has taken an object from a SmartKey Locker cabinet can be denied egress from the facility until the object is returned – and selected management can be alerted automatically via email if an item has not been returned.
By designing SmartKey Locker systems with the ability to communicate across systems, Morse Watchmans helps our customers maintain best-in-breed security solutions without the need to overhaul or replace costly installations. These electronic locker systems have a built-in RS-232 communications port for direct connectivity to printers or other devices, or networked connectivity via Ethernet.
It’s easy to expand scalable SmartKey Locker systems as your needs grow. Start with a single cabinet, or configure your system with multiple locker cabinets. Designed with scalability in mind, each additional metal locker storage unit can be controlled by a single console and monitored by the advanced Key Pro software.
- Notebook PCs
- Weapons
- Cell Phones
- Cash Trays
- PDAs
- Data Terminals
- Hand-Held Radios
- Personal Items
A variety of access control devices to interface with
Like a door to a building or room, the KeyWatcher stands by waiting for a valid signal from your preferred method of access validation. Designed with a built-in keypad with the capability of assigning up to 2,000 User Codes with PINs (Personal Identification Numbers).

The KeyWatcher comes standard with a 2-Line 16-Character each LED and 12-key keypad. Users enter a 4-Digit UserID and a 4-Digit PIN.
Card Reader Login Option

Your choice of magnetic card strike or proximity RFID card readers and be integrated to eliminate entry of UserID. The system can be configured to optionally require a PIN number with the card read
Relay Input Option
The Relay Input Interface will work in conjunction with your card access system. It allows our keypad to only turn on when your card access system creates or closure after it verifies that a valid user is allowed to use the KeyWatcher. valid reply from your access control system.
How it works:
The KeyWatcher has an input connection on the optional Card Reader/Relay board. This normally open input is monitored by the board. When there is a momentary closure between the RLY and GND connections, the system will unlock the touch screen and allow login input.
Login Input methods allowed after unlocking:
- Fingerprint scan
- Secondary card reader directly interfaced with the KeyWatcher
- Single card reader: The weigand wiring can be split to connect to your access control system and directly to the KeyWatcher. The 1st card swipe would unlock the KeyWatcher and allow for a 2nd swipe on the same card and reader to login to the KeyWatcher for key access.
Note: Once the relay input is activated, the system will be unlocked waiting for a login for 10 seconds. If no activity is detected, then the system will relock waiting for the relay input.
Example of Use:
- If the KeyWatcher is in an active area or has public access where the system could be subject to tampering.
- A card reader connected to an access control system would be placed next to the KWTouch.
- The access control system would need to verify the card swipe, then make a momentary closure across our relay input contacts. This would activate our system.

Radio Locker

Single Locker Module

PC Locker

Dual Locker Modules
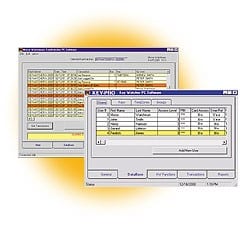
Optimize Performance Capabilities and ROI with KeyPro Software

Maximize your key management system with user-friendly KeyPro software. A PC application with remote access capabilities, KeyPro lets system managers establish permission levels for each User Code and monitor data from any desktop connected to the network.
The software can run activity reports, sort based on different criteria, view and print reports, and more. System managers can generate practical management reports, which trace key movements by time, date and user code. An audit trail report indicates the time and date of every key accessed by a user for a given time parameter.
A built-in scheduler automatically downloads all data to a secure PC, allowing system managers to sort and analyze information to maintain maximum control of access and security issues.
KeyPro III Features
- User-Friendly Interface - Easy to use graphical interface makes programming and running reports quick and simple to do.
- Real-time Transaction Polling - A built-in scheduler automatically downloads all KeyWatcher data to centralized or remote computers.
- Maximized Network Capabilities - With KeyPro III's networking capabilities, sensitive database files can be kept on a network server. This also allows for any installation of KeyPro III to have the ability to make changes and synchronize the data with the KeyWatcher system.
- Extensive Key Management Reporting - Reports can be generated based on specific key, user or alarm transaction. KeyPro provides comprehensive reporting methods, including the ability to sort by last name, first name, ascending and descending sequential order.
- Local Area Network Access - Accessibility to the key management systems over a LAN enables managers to perform functions on any KeyWatcher via TCP/IP.
- The key management systems offers the capability to send email alerts to security managers, keeping them informed of the whereabouts of Smart Keys.
Another key feature of the software is the built-in scheduler. This tool automatically downloads all data to a centralized DB, allowing system managers to sort and analyze the information so they maintain maximum control of access and security issues.
For high-volume key users requiring efficient, secure key storage and complete, real-time accountability. These systems make tracking large quantities of keys — manageable.
Real-Time Reporting
Detailed, real-time management reports based on specific key, user and alarm transactions.
Generate reports by:
- List of keys
- Users
- Keys in use
- Keys removed
- Keys overdue
- ...and Much More
Remote Access
Accessible by multiple administrators from remote locations via standard Internet connection.

